We’ve extensively covered backups in our previous articles on the Ultimate Guide to Backup and Windows Backups, however, let’s reiterate the obvious: backups are needed in case you lose your computer, your precious files, uncommitted code, etc. so that you can restore this data in the future when needed.
In this article, we’ll go further and explain what encrypted backup means, how it differs from a regular backup, what types of encrypted backups are available, and if there’s any software that can help you encrypt your backups. By the end of this article, we’ll look at the different implementations of encrypted backups.
Encryption
Encryption is the process of encoding information, which converts the original representation of information, known as plaintext, into an alternative form known as ciphertext. Only authorized parties can decipher ciphertext into plaintext to access the information.
Encryption doesn’t prevent interference but denies the intelligible content to a would-be interceptor. For example, if someone steals your computer, and removes the hard drive to connect to another computer, its contents can’t just be read as would be the case with any unencrypted drive.
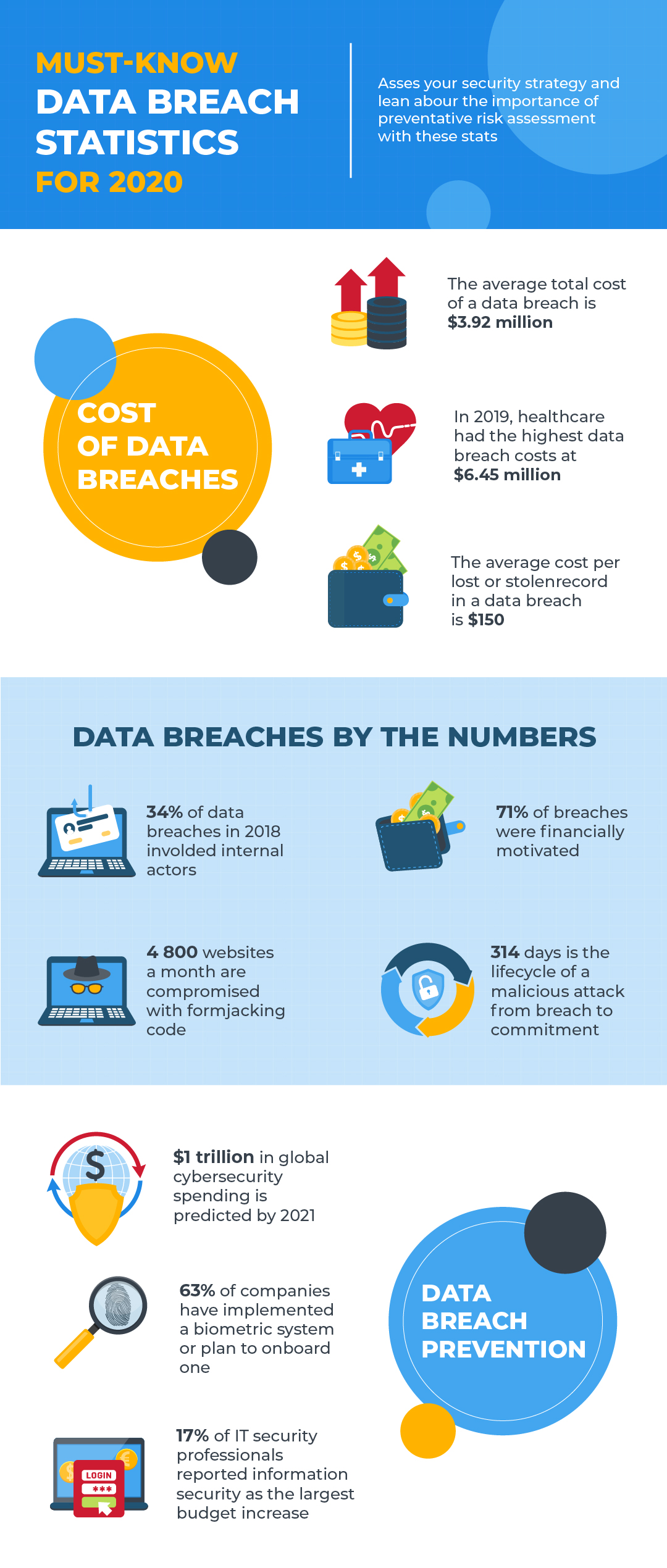
Challenges with encryption
The biggest challenge with encryption is historical that people aren’t using it. However, in 2020, making sure your Windows, Mac or Linux system is encrypted is easy.
Apple encrypts macOS and iOS devices by default, but you normally need to manually select encryption for Windows 10 and Linux systems, and for safety’s sake, it’s worth doing. It’s also possible to encrypt backups, as we’ll see below, where there’s plenty of extra information.
What does encrypted backup mean?
Encrypting your backup means translating a backup’s language into a secret language with you holding the key to the data, with that key a password of your own design. Meanwhile, the encryption algorithm scrambles the data into an unpredictable format. When you need to recover your data – all you need is the password you chose when encrypting your backup – and it’s very important not to lose this password. However, it’s not just a password, it’s another level of protection that guarantees the safety of your data even if your laptop or phone gets stolen or lost.
Types of computer encryption
Three major encryption types are DES, AES, and RSA. There are other kinds of encryption as well, but those named above are the major ones.
DES history goes back to the 1970s and is no longer considered safe on its own. It encrypts just 56-bits of data at a time, which could be easily hacked. It was the standard for some time, but has now been obsolete for many years.
3DES is a version of block cipher used today. As its name implies (3DES stands for Triple Data Encryption Standard) works by using three separate 56-bit keys for triple protection. The downside is that it takes longer to encrypt data; also, even though blocks are encrypted three times, they can still be hacked.
Although some institutions might use 3DES internally, the industry is moving away from it.
AES encryption
AES, which stands for Advanced Encryption Standard, is used by governments and security organizations for classified communications. AES uses “symmetric” key encryption, which means that someone on the receiving end needs to have a key to decode the information.
AES is now still the most widely used and accepted encryption method.
RSA encryption
RSA stands for Rivest-Shamir-Adleman. It’s widely used for data sent online and relies on a public key to encrypt data. Those who receive the data will have their own private key to decode the message. That’s the best way to transmit data for parties who might not know each other without compromising each other’s sensitive data.
People use RSA to verify a digital signature and ensure the person on the other end is legitimate. Due to the difficulty of encrypting data this way, it’s not practical for large or numerous files.
Other encryptions
There are other encryption types and services available such as fish(es) (Twofish, Blowfish, Threefish). Those different services use different tech which is popular among developers but is generally not known to average consumers.
Difference between encrypted and unencrypted backups
Let’s explain the differences between encrypted and unencrypted backups by giving an example of iPhone backups.
One major difference between encrypted and unencrypted backups is that there’s additional information that’s stored in the encrypted backup but not included in the unencrypted. Such information includes website history, personalized settings (including wi-fi settings and health data), and passwords. To restore an encrypted backup, you’ll also need a password, which is not required for syncing or backing up but only in case of restoring your data.
Types of encrypted backups
Individual file and folder encryption encrypts only specific items that you ask the system to. This method is acceptable if there are relatively few documents stored on a computer.
Volume encryption creates a container of sorts where all files and folders saved to that container are fully encrypted.
Full-disk or whole-disk encryption is the most complete form of computer encryption since all files, folders, and volumes on the disk are encrypted. When powering your computer, you’ll need to provide an encryption passcode or encryption key (stored on a USB device, for example) to unlock your files.
Encrypted backup cloud
Let’s see how major cloud providers secure our data.
Dropbox, for example, is designed with multiple layers of protection that are distributed across a scalable and secure infrastructure. Dropbox files at rest are encrypted using AES 256. The provider uses SSL/TLS for data transmission between Dropbox apps and its servers. SSL/TLS in turn creates a secure tunnel protected by AES 128. There’s also a two-step verification for an extra layer of security at login. Dropbox doesn’t provide for client-side encryption and doesn’t support the creation of your own private key. However, users can add their own encryption, for example, with a third-party application at both the file and container level. All files served on the Dropbox server are encrypted.
With OneDrive, files are already encrypted at rest and in transit. With Personal Vault (the new security feature introduced in 2019), there’s now another layer of optional security features on top. In the OneDrive app, you’ll find the Personal Vault folder, which you can use to store your most important files or files with the most sensitive data.
iCloud secures your information by encrypting it while it’s in transit, storing it in an encrypted format, and using a secure token for authentication. For sensitive information, Apple uses end-to-end encryption, with sensitive information including card transactions, home data, health data, iCloud keychain, payment information, browsing history, Wi-Fi passwords, W1 and H1 Bluetooth keys among other data.
However, Apple retains a key to this encryption, and if requested by Government order, can decrypt this information to provide if ordered by a court, which is why Apple still allows you to maintain an encrypted backup of your iOS device on your computer, backed up using iTunes
Messages in iCloud also use end-to-end encryption, and if you have iCloud backup turned on, your backup includes a copy of the key protecting your messages. End-to-end encryption requires two-factor authentication turned on for your Apple ID.
Encrypted backup drives: SDD, HDD and USB
Let’s see how you can encrypt your external hard drive on macOS and Windows.
Encrypting the external hard drive
Encrypted backup macOS
First of all, ensure your disk is properly formatted for macOS – acceptable formats include HFS+, APFS, Mac OS Extended (Journaled).
If not, then you should appropriately format it as follows: type Disk Utility in Spotlight Search → Select your external drive → Click Erase → Click the Format from dropdown → from the list of formats choose Mac OS Extended (Journaled) or APFS → Enter a secure password → Click Choose → Click Erase. The Drive is now reformatted and encrypted.
There’s another option to encrypt using FileVault.
Locate Time Machine and rick-click the icon → Choose Encrypt Time Machine → enter a secure password → Click Encrypt Disk → After the process is complete, verify the encryption by selecting the drive in Disk Utility.
Encrypted backup Windows
For Windows, the procedure is almost similar: at first, we have to make sure the external drive is properly formatted. Follow the steps:
- Open File Explorer → right-click your External Drive → Select Properties
- Under the General tab find File System and verify it says NTFS. If it doesn’t, go to step 5
- Return to File Explorer → right-click your External Drive → choose Turn on Bitlocker.
- Select Use a password to unlock the drive → enter password → click next
- If under step 2, File System doesn’t mention NTFS, you’ll need to Format the disk. Follow the steps below
- Open File Explorer, right-click on your external drive and choose Format.
- Click Ok.
- Now, ensure the drop-down under File System is NTFS, then click Start.
- After your drive is formatted, click ok, and return to step 3.
Now, let’s take a moment to discuss SSDs and the peculiarities of SSDs encryption on various OS.
SSD encryption
Since SSD (or Solid State Drives) are now practically everywhere, the process of encrypting your backups on them is just as straightforward: in Windows, turn Bitlocker Drive Encryption and FileVault on Mac.
However, the nature of flash makes it more difficult to encrypt or erase data on SSDs than traditional hard drives.
Nevertheless, hardware-based disk encryption makes it easier to encrypt and erase SSDs securely without any load on the host processor.
Because of the wear-leveling algorithms that are integral to modern SSDs, data remnants are spread out across the drive, making it more difficult to destroy sensitive information without erasing the whole drive.
However, some enterprise and consumer SSDs have hardware-based disk encryption, where data is secured with AES, and encryption is handled by a dedicated cryptoprocessor.
Authentication with encrypted SSDs happens pre-boot — everything (including user space data, OS) is completely inaccessible until the user is authenticated.
What’s even more interesting is that sanitizing encrypted SSDs is fast and secure. On an encrypted SSD, it can take less than a second to change the encryption key, rendering all data on the drive unreadable and useless.
Unlike software-based encryption solutions, encrypted SSDs are OS-agnostic meaning they can be used on Linux, Windows, macOS.
Many SSDs and other hard drives claim to be self-encrypting. Prior to Sep 2019, Windows Bitlocker didn’t perform any encryption on those SSDs even if a user enabled Bitlocker manually.
In theory, it was supposed to be good, since the drive could perform the encryption itself at the firmware level, thus reducing CPU usage, speeding up performance, saving power, and whatnot.
But it was not the case — drives ended up with missing or empty passwords and other terrible security failures.
Now, after Sep 2019, Microsoft changed the game. Bitlocker ignores drives that claim to be self-encrypting and does the encryption work in software.
The change became effective as of Windows 10’s KB4516071 update, released on September 24, 2019.
To ensure your Bitlocker is using software encryption as opposed to hardware encryption, you shall disable it and enable it again. You may look at the following Microsoft software bulletin to check if you’re using hardware/software encryption.
Now, let’s talk about encrypting a USB flash drive.
Encrypting a USB flash drive
Suppose you backed up your files on a USB flash drive. Now, if you want to prevent sensitive data on that drive from falling into the wrong hands, you can securely encrypt your flash drive within Windows so that data stored on it cannot be read and accessed without entering a secure password.
Follow the steps:
- Insert your USB flash drive into your Windows PC
- Open File Explorer
- Locate your USB flash drive, right-click on it and Turn on Bitlocker
- From the prompt, select Use a Password to Unlock This Drive
- Come up with a secure password
- When asked How do you want to store your recovery key, choose to Save the recovery key to a file. Save that file to a secure location that only you have access to. This file doesn’t contain your password.
- If available, select Encrypt Used Space Only
- Windows will securely encrypt your USB flash drive, this will take a few minutes.
Now, if you want to use your encrypted USB flash drive, plug it into your computer, and when prompted with a password, enter it to unlock your drive. If you decide to disable your encryption, simply manage your preferences through Manage Bitlocker.
Encrypted backup software
You may check the review of some of the following and other backup software in our previous article: Ultimate Backup Guide and Windows Backup Guide [insert links here to the previous articles]
In this piece, we’ll only concentrate on encryption features and capabilities of the following tools and programs.
Paragon Backup & Recovery Community Edition
Paragon Backup & Recovery community edition is a free backup solution from Paragon (you may check Hard Disk Manager paid option) that’s focused on providing basic yet very functional backup solutions for both image and file backups and allows for scheduling, encryption, compression to boot. There’s a good set of file encryption options from setting a password to selecting the method of encryption to use.
Genie Backup Home
Genie is a powerful backup tool that has a huge number of options for creating and saving backups. In addition to internal/external media, a user can configure saving to remote media via FTP or Amazon servers integration.
There are built-in utilities that save critical info from third-party apps like Outlook and Windows Mail. Sensitive information is protected in backups with 128, 192, 256-bit AES encryption
Since we have not mentioned the following software in previous articles on the subject, let’s briefly outline its main features, including encryption:
Iperius Backup
- Incremental & differential backups
- Local & remote server options (including virtual machines)
- Backup to NAS/RDX, Google Drive, Amazon S3, Azure Storage, OneDrive, Dropbox
- AES data encryption
- Scheduling & logs
- Individual files restore
- Copy locked files with VSC (volume shadow copy)
A different implementation of the encrypted backup
Encrypted backup iPhone, iPad, iPod & iTunes
To protect your backups on the aforementioned iOS devices you can use password protection and encryption.
The Encrypt backup feature in the Finder or iTunes encodes your information. There’s a difference between encrypted and unencrypted backups in that encrypted backups can contact information that unencrypted don’t, such as your saved passwords, wi-fi settings, website history, health and call history. What encrypted backups don’t include are Face and Touch IDs, as well as device passcodes.
Your backup isn’t encrypted by default. Therefore to encrypt it for the first time, you’ll need to turn on the password-protected Encrypt Backup option. Backups will be automatically encrypted from then on. If you backup your data in iCloud, it gets automatically encrypted.
Let’s walk you through the process:
- On Mac with macOS Catalina 10.15 (for earlier versions just open up iTunes), open the Finder
- Connect your device to the computer with the USB cable
- Locate your device on your computer
- From the General tab (or Summary tab), select Encrypt local backup under the Backup section.
- After prompt, make a password, your backup will start and override all your previous backups.
According to an article published in Jan 2020 in Technology News, Apple Inc. dropped its plans to allow users to fully encrypt backups of their devices in iCloud after the FBI complained that the move would harm the investigations. Instead of protecting all of iCloud with end-to-end encryption, Apple chose to protect only the most sensitive data such as saved passwords or health information.
Encrypting your Windows system drive
Microsoft Bitlocker is a disk encryption tool included in Windows 7 (versions: Enterprise and Ultimate), Windows 8.1 (versions: Pro and Enterprise), and Windows 10 (except Home Edition). Bitlocker is designed to work with a Trusted Platform Module chip in your computer, however, it can work even without a chip provided a few settings are configured within the operating system which requires administrative privileges.
To enable Bitlocker, follow the path:
Type in the search field: File Explorer; in the left-hand panel find disk C and right-click on it. If your version supports Bitlocker, then click on it to enable the program. When you enable Bitlocker, Microsoft prompts you to save a copy of your recovery key (very important step since you’ll need the recovery key to unlock your disk). There are a few options to save your key: you can print it or save it in a Microsoft account or file. Bitlocker lets you require a PIN at startup.
There is another option to bypass BitLocker and that is to use the open-source VeraCrypt tool to encrypt your Windows system drive.
In Windows 10, you can either use Bitlocker (which is not available in Home Edition) or turn device encryption.
Let’s turn on device encryption first. Follow the steps:
- Sign in to Windows under admin account
- Select Start → Settings → Update and Security → Device encryption [if you don’t see that option then it’s not available]
- Turn on [if it’s turned off]
For Bitlocker, follow the path
- Sign in to your Windows device with your admin account
- In the search box on the taskbar, type Manage Bitlocker [otherwise Start → Windows System → Control Panel → System and Security → under Bitlocker Drive Encryption select Manage Bitlocker]
- Turn on Bitlocker and follow instructions.
On Windows 10 PC, Personal Vault also sets up Bitlocker-encrypted area on your local hard drive to sync your Personal Vault files
Encrypted backup Mac
Modern Macs already encrypt the system drive, but to ensure macOS Catalina 10.15 is encrypting its Time Machine backups, follow these instructions:
- Turn on Time Machine → add a backup disk [or change to a different one; also — adjust other settings if necessary]. Time Machine can’t back up to iPod or a disk formatted for Windows [Windows formatted disk, however, can be reformatted (by permanently removing all data) to a Mac file system format and used as a backup disk]
- For increased security, select Encrypt Backups [Encryption might not be available in case the disk you’re using is formatted using an Apple Partition Map (AMP) or Master Boot Record (MBR) partition and the disk has more than one partition]
- Click Use Disk
- If you set up another disk, click Replace or Use Both
- If you’re prompted to reformat the disk, either reformat it or choose a different disk
- Type a password for the backup disk [for Encrypted backups]
Encrypting your Linux system drive
In Linux, you encrypt the disk during the installation of the operating system, using a tool named dm-crypt or any other third-party tools designed for just that. You can encrypt basically anything with OpenSSL using various algorithms. There are encryption tools/programs available and most of them are dependent on the OpenSSL library.
If you have found a spelling error, please, notify us by selecting that text and pressing Ctrl+Enter.



Leave a Comment